
Despite an ever-changing digital world, email remains one of the most popular forms of communication. As a result, cybercriminals continue to develop new and creative ways to scam you out of personal or customer-sensitive information. Today, we’re going to cover how to prevent phishing scams and other forms of cyberattacks by tackling one of the most common ways this happens: website links.
Suspicious links are so common online that most of us are uneasy about clicking on any links in almost any situation. So how do you stay safe without suspecting your mom or business partner of a phishing scam when they send you a link to something like a new recipe or the latest Forbes article? Learn how to read URLs!
You may be thinking “Surely this can’t still be happening.” This cartoon from The New Yorker suggests otherwise.

So what can you be looking for to tell if a URL you’ve been sent is valid? Below are a few strategies to consider:
1. The Domain is Misspelled
Altering the spelling of domains is one of the most common ways cybercriminals implement phishing scams. Take a look at the URLs below and see how long it takes you to spot what’s wrong with them:
- www.intrelaced.io
- www.rnsnbc.com
- www.face0ok.com
- www.linedn.com
Number 1: Letter Scramble – when letters are scrambled inside longer words, our brains can correct them without us noticing.
Number 2: Letter Combos – this one isn’t as common as the others due to the wide number of fonts used today. In this case, the “r” and the “n” look a lot like the letter “m.”
Number 3: Number Swap – no doubt the “o” vs. “0” issue has caused problems for you in some way before. It’s also a classic method used to mask a shady URL.
Number 4: Missing Letters – this one doesn’t work on most well-known URLs, but for some longer domains, it can be very tricky to spot.
2. Domain Jumble
This method has become much more popular over the past few years. Ultimately, you should always be looking for the top-level domain in any link before you click. To do this correctly, follow these two rules:
- If there aren’t any single forward-slash characters in the URL (/), then read the top-level domain from left to right
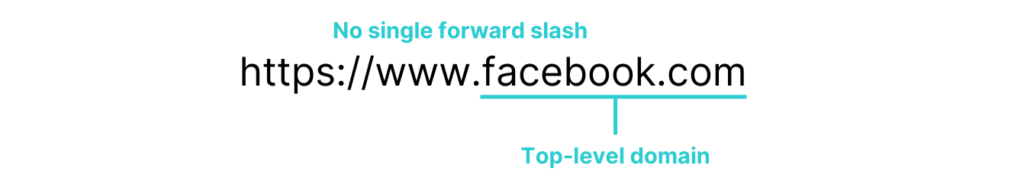
2. If there are single forward-slash characters in the URL (/), then locate which one is the farthest from the right. Starting from that forward slash, read the top-level domain from right to left
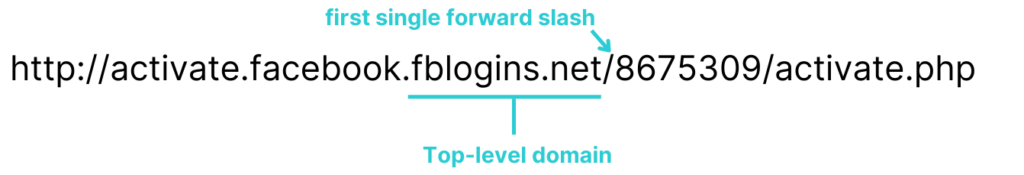
Pro Tip:
We are looking for single forward slashes in the URL. Therefore, the double forward slash in HTTP:// would not apply.
Test it out! Take a look at the URLs below and see if you can see what links are good and what links are bad
- www.business.facebook.com/login
- http://activate.facebook.fblogins.net/8675309?login.php
- www.facebook.login.com/account
- www.facebook.com/ads/library/?active_status=all&ad_type=political_and_issue_ads&country=US&media_type=all
Number 1: Good – the forward slash is between login and com, so the top-level domain is facebook.com
Number 2: Bad – the forward slash is between 8675309 and net, so the top-level domain is fblogins.net, not Facebook
Number 3: Bad – The forward slash is between com and account, so the top-level domain is login.com, not Facebook
Number 4: Good – the forward slash is between ads and com, so the top-level domain is facebook.com. We’ll explain the meaning of the rest of that URL towards the end.
3. Short Links
Short links are fairly common on social media and in some cases, in emails, for several reasons. Some of the most common resources for this are Bitly, Rebandly, and TinyUrl. Companies and marketers use short links to reduce character counts on social media, track link clicks, etc. Because of their common usage, they have also started to be leveraged in cyberattacks. Here’s an example of a short link: https://bit.ly/3fh8Dmo
So how do we protect ourselves? Social media platforms carefully scan linked websites for authenticity, quality, and relevance to the ad itself to ensure it’s not misleading or malicious.
As for email, we need to be a bit more careful to prevent phishing scams. If the short link is being sent from a source you don’t trust quite yet, then you can copy/paste the short link into online tools that will expand it for you. Some of the most popular sites for expanding short links include:
UTMs & Tracking
Lastly, let’s talk about the mess you often see at the end of links like this:
https://interlaced.io/2022/02/11/remote-it-management-and-culture/?utm_source=blog&utm_medium=reading_urls&utm_campaign=remote_it&utm_term=example_link&utm_content=reading_utmsFirst and foremost, if you follow the single forward slash method, then you can focus on what matters. In this case, you can see that the top-level domain is Interlaced.io, so the rest doesn’t really matter. For those of you who are curious (although we understand most marketing people are familiar with these), here’s what it all means!
Everything after the question mark – ?utm_source… – is simply for tracking purposes. It just helps businesses understand where their website traffic is coming from. In this example, here’s the information a company would gather:
- Campaign Source: Blog
- Campaign Medium: Reading URLs
- Campaign Name: Remote IT
- Campaign Content: Reading UTMs
That’s it! UTMs can definitely be used to better mask sketchy URLs, but if you follow best practices laid out in this article, they’re completely harmless.
Phishing Indicators You Can Ignore
While it’s important to be vigilant and use caution when clicking links in an email, there are a couple of signals that while once thought to be indicators of phishing, are no longer valid:
- Misspellings or poor grammar: as people are often multitasking and moving quickly, you are more likely to receive a completely legitimate email that includes bad spelling or poor grammar than a crafted phishing attack.
- Hovering over a link to determine legitimacy: tools like Proofpoint can rewrite links as a security measure and will reroute users if the destination is unsafe. Likewise, it can be difficult to hover over links on mobile devices, which is where most people are reading emails now.
Put your new skills to the test – Google’s Phishing quiz challenges you to see if you can spot when you’re being phished.
Unfortunately, there are other cybercriminal methods such as “onMouseover” event triggers, Punycode DNS registrations, and more. And if it feels like you’re having to learn a new language just to understand what’s going on, we’ve put together this handy guide full of cybersecurity terms to help keep you and your teams safe.
Let us build a comprehensive security program for your business or organization. Talk to our team today: business@interlaced.io.
